Top Cyber Security Ads to Learn From Trend Micro. The hackers claimed that they had encrypted Camparis servers and downloaded two terabytes of its private information.
 Kpmg Cyber Security Grow Your Business With Cyber Confidence Tay Kok Wei S Works
Kpmg Cyber Security Grow Your Business With Cyber Confidence Tay Kok Wei S Works
In weighing the benefits and security risks of ADS-B the aviation industry would benefit from understanding cybersecurity problems that have emerged with parallel technologies in other transportation domains.

Cyber security ads. In this hilarious Norton Internet Security ad watch as a cyber criminal portrayed by Dolph Lundgren tries to hack your bank account represented by a pretty little unicorn and how Nortons Internet Security software puts Dolph in his place. Pam Rowland an assistant professor of cyber security at Dakota State University and co-founder of outreach organization CybHER many organizations need to overhaul their job ads to attract diverse candidates. According to Dr.
Weve found that numbers and statistics on paid ads are often excellent attention-grabbers. It gives the pilot a. For one firms should abandon highly.
Individual Contributor Business Unit. Some cyber security companies may avoid using paid campaigns due to the competitive nature of paid advertising in the cyber security space. Thats understandable if you dont know what youre doing its easy to spend thousands on cyber security ads and get nothing in return.
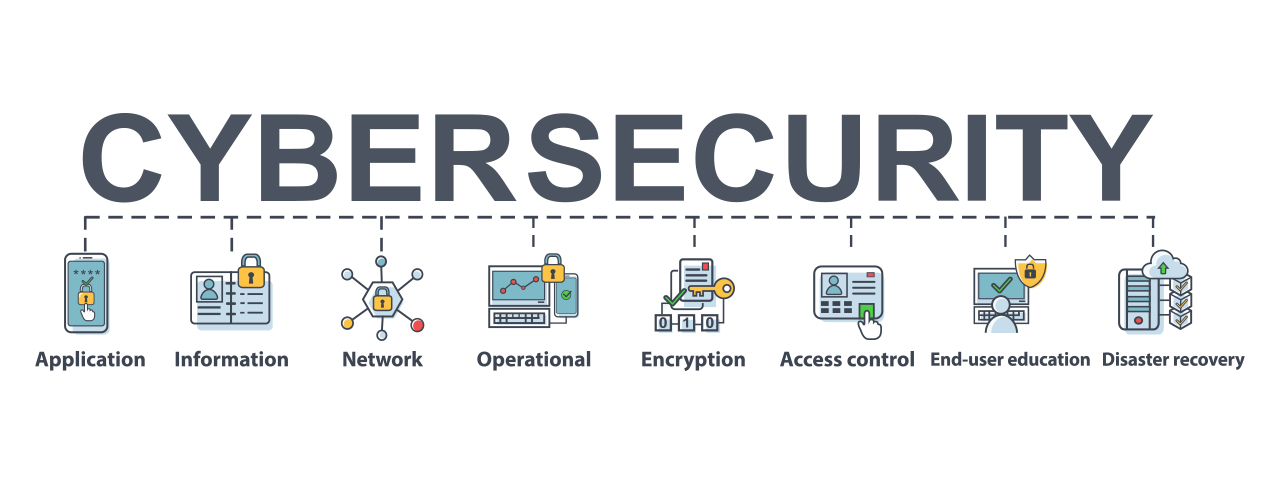
Automatic Dependent Surveillance Broadcast ADS-B is a technology mandated in all commercial and general aviation aircraft by 2020. Cybersecurity is the art of protecting networks devices and data from unauthorized access or criminal use and the practice of ensuring confidentiality integrity and. What would the world be like without cybersecurity.
First it uses intriguing stats to capture attention quickly. Senior Cybersecurity Planning Analyst - Cyber Portfolio Management Office PGE Corporation San Francisco CA US Not Specified Requisition ID 90084 Job Category. Mit Cybersicherheitsmaßnahmen werden die Daten und die Integrität der Rechenressourcen geschützt die sich in einem Unternehmensnetzwerk befinden oder damit verbunden sind.
Traditionell bestand Cyber-Security aus einer Hardware die als Firewall als Teil eines Business-Servers bezeichnet wird. Second the copy is short and to the point and focused on the value to the viewer. Though ADS-B is expected to significantly improve overall aviation safety and security it is not expected to be completely free of security vulnerabilities.
ZVg Zugleich wollen die Organisatoren auch zeigen wie man mit einfachen Mitteln und geringem Aufwand viel zur Sicherheit im Web beitragen kann. Mitarbeiter für den Schutz kritischer Infrastrukturen. Als Beispiele werden in der Mitteilung etwa starke Passwörter genannt.
130 Old Street London EC1V 9BD. EASAs role is to ensure that cyber risks are taken into account during aircrafts design development and operation and then controlled in order to avoid adverse effects on citizens safety. Its partner does not feel bad for it because the laptop failed to install its.
Certified Secure Data Workflow Associate. Hiring teams need to think critically and redesign rather than using the same strategies as the past ten years she says. Diese Ressourcen sollen während des gesamten Angriffszyklus vor allen Hackern geschützt sein.
Daniel Nussbaumer Präsident der SISA und Leiter Cyber Security bei T-Systems Schweiz. Ragnar Locker Group ran simple Facebook ads entitled Security breach of Campari Group network The ad shared with the public addressed a press release from Campari that did not fully acknowledge that the company had been hit by a Ragnar ransomware attack. It is on the basis of this interrogation that this film produced by Thales demonstrates some of the impac.
Trend Micro is a big name in the cyber security world known for their solutions research and security blogs. Mon 12 Oct 2020 1240 EDT 2955 A government-backed advert that encouraged people working in the arts to reskill by turning to a career in cybersecurity has been scrapped after. Defending yourself against cyberattacks starts with understanding the risks associated with cyber activity what some of the basic cybersecurity terms mean and what you can do to protect yourself.
To this extent the objective of the Agency is to incorporate cybersecurity in the existing safety notion through promotion training sessions or awareness campaigns regulatory activities as well as. Cyber-Security ist die Wissenschaft von der sicheren Aufbewahrung digitaler Daten und das nur in den Händen derjenigen die auch tatsächlich Zugang haben sollten. In this short Comodo Security ad a poor laptop gets a virus and complains about its ailments.
This ad stands out for several reasons. Information Technology Department Overview The Cybersecurity Portfolio Management Office. Wie ein Passwort nicht nur stark sondern auch sicher ist erfahren.
Third the ad is making smart use of LinkedIn. Accounting Finance Job Level. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy Safety How YouTube works Test new features Press Copyright Contact us Creators.
Bleiben Sie in den einzelnen. For paid campaigns you either need a dedicated in-house person or team with experience in this area or an agency that specializes. Jede erfolgreiche Zertifizierung in den einzelnen Disziplinen der OPSWAT Akademie ist für ein Jahr gültig.
While you may read stories about iPhone security and privacy such as a backdoor flaw in its Wi-Fi chip and how an iCloud account can hold a. Apple uses security advisories and our security-announce mailing list to publish information about security fixes in our products and to publicly credit people or organizations that have reported security issues to us.
 Apple Acts As Digital Transformation Hits Panic Mode Computerworld
Apple Acts As Digital Transformation Hits Panic Mode Computerworld
Kaspersky is a well-regarded name in the field of antivirus protection and it maintains that reputation with its Internet Security for Mac software which positively bristles with features.

Apple internet security. OS X includes a number of security measures to combat malware Gatekeeper XProtect and a built-in Firewall. Bitdefender Internet Security 2020 stores passwords and sensitive information for quick access. However no system is completely foolproof.
These are VirusBarrier and NetBarrier which catch and kill malware. It includes the email address and password you use to sign in as well as the contact payment and security details you use across Apple services. Learn more about security and your Apple ID.
Integos Mac Internet Security X9 suite is a pair of utilities designed to help you keep your Mac safe and running smoothly. Internet Security AntiVirus is designed to provide complete protection for your Mac online offline. It is a next-gen security product to give you protection based on dynamic behaviour based security.
It comes with malware scan adware scan behaviour based WiFi security giving your Mac the most advanced security. Change your Wi-Fi network security settings If you are able to change the security settings on your router youll not only rid yourself of the annoying iOS 14 message but be more secure. Check the documentation for your router for instructions.
Your Apple ID is the account you use to access Apple services like the App Store Apple Music iCloud iMessage FaceTime and more. Apple very quickly shipped security patches to protect against this vulnerability and published a detailed support document that Mac users who handle particularly sensitive data should read. We also credit researchers who have reported security issues with our web servers on the Apple Web Server Notifications page.
Bitdefender Internet Security 2020 delivers multiple layers of protection against ransomware. It uses behavioral threat detection to prevent infections and protects your most important documents from ransomware encryption.
Cyber Security Consultant Consultants in cyber security make an average salary of 91000 and need skills in information security and surveillance asset protection and security operations. Intigriti is an easy-to-use Ethical Hacking and Bug Bounty Platform.
 In Need Of Cybersecurity Experts The Star
In Need Of Cybersecurity Experts The Star
Intigriti is an easy-to-use Ethical Hacking and Bug Bounty Platform.
Who needs cyber security. Our Ethical Hackers are ready to start testing. Try it out today. Our Ethical Hackers are ready to start testing.
These industries will need to up their security. So who needs cybersecurity training the most. Advertentie Strengthen and Streamline Cybersecurity Across Multiplatform Environments.
Microsoft Security Provides Integrated Security with Full Coverage. Penetration and Vulnerability Tester Penetration testers make an average salary of 104000 and need to have skills in penetration testing Java vulnerability assessment and software. Just as there is a global health body the World Health Organization WHO to better understand and combat health threats we need a cyber-WHO to.
It is necessary for modern-day consumers to become aware of the level of cyber security companies or developers of IoT are offering. Sign up now to access engaging shareable content thats available in multiple formats. Advertentie Beperk de kans om doelwit te worden van cybercrime of -spionage.
Cybersecurity risk is increasing driven by global connectivity and usage of cloud services like Amazon Web Services to store sensitive data and personal information. Here are 10 reasons why your organization needs a new cybersecurity strategy this year. Same some peoples are sitting there who knows how to play with technology effectively then the result is going to be dangerous Hack.
Chances are good that your assumptions regarding what youre defending against are wrong or at. Tap into millions of market reports with one search. Along with financial planning smart homeowners must do security planning.
Advertentie Strengthen and Streamline Cybersecurity Across Multiplatform Environments. The role of cybersecurity inside the company can never be ignored. We all need cyber security to secure.
That is why employees will also need to have a security mindset. Advertentie Ensure your organization can protect all its important data from any kind of cyber attack. Without a cybersecurity program your organization cannot defend itself against data breach campaigns making it an irresistible target for cybercriminals.
You need to take proper security measures to stay protected against cybersecurity threats. Because new threats are rising fast. Advertentie Submit your cyber security project today.
If we dont know how to use technology effectively then we are the dumb peoples in my knowledge. Advertentie Unlimited access to Cyber Security market reports on 180 countries. Vindt er tóch iets plaats dan komen onze ervaren adviseurs direct in actie.
You all know about this. Microsoft Security Provides Integrated Security with Full Coverage. Since cyber-attacks are rising at a worrying level year by year around the world.
Advertentie Submit your cyber security project today. Advertentie Compare courses from top universities and online platforms for free. You can hire a professional or IT department to work on the vulnerabilities.
Every business needs to fight cybercrime by strengthening the security of the business. Owners should take an inventory of and know all of the various network-connected devices in your home. Free comparison tool for free cyber security training.
Data shows that the larger the firm thus the prone it is to be attacked. Try it out today.
The name is a reference to a physical sinkhole. The Cybersecurity and Infrastructure Security Agency CISA has the mission to provide a common baseline of security across the Federal Civilian Executive Branch FCEB and to help agencies manage their cyber risk.
 Sinkhole Attack Scenario Download Scientific Diagram
Sinkhole Attack Scenario Download Scientific Diagram
A sinkhole redirects or blocks traffic meant for a destination.

Sinkhole cyber security. First EINSTEIN detects and blocks cyberattacks from compromising federal agencies. Dabei werden die durch Analyse von Schadprogrammen ermittelten Domainnamen in Zusammenarbeit mit den zuständigen Domain-Registrierungsstellen auf Sinkhole-Server umgeleitet. According to the bulletin the sinkhole.
The sinkhole listens to the Internet for infections 247 instantly detecting if an infection record is dangerous to your company and finding threats that your existing IT security solutions anti-virus firewalls etc may miss. Most common to security professionals is a DNS sinkhole 1. In particular the bulletin notes concerning activity coming from a sinkhole Sinkholes are used by researchers to capture bad internet traffic mostly coming from botnets and block infected machines from carrying out their orders.
Owning a sinkhole network means that we can intercept communications as they come back outside of the network. For example they will often register groups of IP addresses that effectively. Sinkhole Definition of sinkhole.
Shannon Vavra dug into that bulletin and found the story behind it to be a very confusing mystery. This common baseline is provided in part through the EINSTEIN system. A company or the government can also go through the courts to get control of a.
If it received a response from the domain it shut down. WannaCry included code that looked to check if a specified domain had been registered. Ein gängiges Verfahren zur Identifikation mit Schadprogrammen infizierter Systeme ist die Umleitung solcher schädlicher Domainnamen auf sogenannte Sinkholes.
In the case of WannaCry a researcher using the pseudonym MalwareTech ended up accidentally activating the kill switch when he tried to create a sinkhole in order to study the software. EINSTEIN serves two key roles in FCEB cybersecurity. The larger the Security Zone the larger the throughput and the greater number of Cyber Threat Intelligence feeds that can be integrated.
Maßgeschneiderte Lösungen und Services zur Verteidigung Ihres Unternehmens gegen Cyberangriffe. The Torpig bots checked in with the sinkhole every 20 minutes or so and the researchers did find that if they looked at traffic for any given hour the number of unique IPs did closely match the number of unique bots. This computer masquerades as one of the C2 command-and-control servers in the botnet so that DNS requests from compromised computers in the botnet for this server are re-directed to the sinkhole computer where they can be analysed by researchers.
We found the Ozdok bots checked in about every 5 minutes so. That is what gives us insight into what is happening inside. What is a DNS Sinkhole.
If not it continued to work. There are many ways to create a sinkhole. Provides real-time JSON data on cyber-attacks allowing organizations to mitigate risks as they arise.
This technique can be used to prevent. Sinkhole A sinkhole is a computer used by anti-malware researchers to collect information about a botnet. A single infected system is likely to keep the same IP address for a given hour.
They are used by the security community to stop botnet traffic phishing and other bad activity. The altered destination is known as the sinkhole. Building a sinkhole network depends on cyber-criminals working in certain ways and exploiting that.
DNS Sinkholing is a mechanism aimed at protecting users by intercepting DNS request attempting to connect to known malicious or unwanted domains and returning a false or rather controlled IP address. Noun A standard DNS server configured to hand out non-routable addresses for all domains in the sinkhole so that every computer that uses it will fail to get access to the real website. Dabei werden Anfrage auf eine vom Administrator festgelegte IP-Adresse umgeleitet eben jenes Sinkloch.
An ISP can simply divert traffic from the IP address nameserver you see in Whois to another. The controlled IP address points to a sinkhole server defined by the DNS sinkhole administrator. The Evolve DNS Sinkhole solution can be configured for high-throughput by simply increasing the size of your Evolve Security Zone.
The founder of Liberty Reserve a digital currency that has evolved as perhaps the most popular form of payment in the cybercrime underground was. Als geeignete Abwehrmaßnahme empfiehlt sich DNS-Sinkholing. Diese IP-Adresse verweist auf einen Sinkhole-Server.
Security experts who have examined the bulletin tell CyberScoop they cant explain whats technically detailed and it provides no solutions to remedy the problem. A botnet sinkhole is a target machine used by researchers to gather information about a particular botnet. Sinkholing is the redirection of traffic from its original destination to one specified by the sinkhole owners.
In April a small agency under the DOD released a bulletin that said a Chinese hacker group had been stealing data from cleared contractors via a leaked sinkhole. It is also used by security researchers to collect information about botnets activities and the adversaries PPTs. A sinkhole is a system used by security teams to fight block and collect information about adversaries infiltrated the organization.
This might not be new to your ears but a panic room is basically a secured chamber where anyone can stay put in the event of a security threat. For non-celebrity clients who desire celebrity-level police response and safety it is possible to choose a system which is simple secure and can be managed easily without paying celebrity prices.
 Hollywood S Bodyguards Inside The World Of Celebrity Security Detail Abc News
Hollywood S Bodyguards Inside The World Of Celebrity Security Detail Abc News
Recordings from these cameras are routinely utilized by our security teams and made available to investigative authorities as requested.

Celebrity security systems. Посмотреть видео о том как мы работаеми. Wir verwenden Cookies um Inhalte und Anzeigen zu personalisieren Funktionen für soziale Medien bereitzustellen und die Nutzung unserer Webseite zu analysieren. The more elaborate systems.
3 Angelina Jolie and Brad Pitt. Celebrity Systems Corporation A Vellicom Company 1046 Calle Recodo G San Clemente CA 92673 Contact Point. Our marine safety record over our 42-year history clearly illustrates our commitment to the safety of the millions of guests and crew that sail on our ships.
Below are some of the security measures celebrities have taken. To apply text SIS to 57682. The World Protection Group WPG was founded with celebrity and VIP protection in mind drawing first on WPG President Kent Moyers many years experience as an elite bodyguard at the Playboy Mansion in Los Angeles California.
They are estimated to spend about 2 million dollars a. Find your next job near you 1-Click Apply. These systems are upgraded as new technologies are developed.
S Celebrity Systems - AV IT Solutions Provider. Our vast knowledge of the friction couple and not just a single element sets us apart. Drone security and investigation services.
Celebrity Systems Corporation Contract Number. There security system for their home is also rumored to cost in the millions of dollars alone. Provides unique security solutions to Fortune 500 luxury brands and tech companies special events and celebrity clients.
From its roots in the British automotive industry Celerity Systems offers the most integral wheel end. Celebrity VIP Security Protection Services. AS Solution is a security company dedicated to keeping our clients safe.
Безопасность аккаунтов в соц. 2 MillionYear Brangelina is the nickname used for the high profile couple of Brad Pitt and Angelina Jolie. Celerity Systems is built on over 80 years of experience in the friction and foundry industries.
Regardless of whether you are on holiday shopping at a movie premier or attending a party we are your personal security company for the job. Some celebrities like George Clooney and Amal Alamuddin have added a panic room to one of their homes. Safety Security For Celebrity Cruises and parent company Royal Caribbean Cruises Ltd the safety and security of our guests and crew is our highest priority and fundamental to our operations.
Browse 17 CELEBRITY SECURITY Jobs 28K-127K hiring now from companies with openings. GS-28F-0011M Packaged Room Environments999-93-D-6082 Contractor. Some chambers feature bullet-proof and even bomb-proof doors access to a phone access to security system footage and food supplies.
Celebrity has closed-circuit television cameras located in hundreds of strategic public locations throughout the ship but not in private staterooms public restrooms or private spa areas. Drone cameras can provide superior coverage to stationary or CCTV security cameras. 800-992-9039 949-369-3990 949-369-3995 FAX.
While we cant provide bodyguards Deep Sentinel provides smart home surveillance without the pricetag but with all the dedicated security and privacy of a celebrity-level system. Los Angeles-based firm Strategically Armored Fortified Environments designs systems for chief executives celebrities and political figures. They have a 360-degree view they are generally out of reach of disabling attacks and they can follow suspects or persons of interest as they move.
Primary point of contact for the principal for overall protective physical security. GS-07F-9998H General Products GSA. Diese Website verwendet Cookies.
Welcome to Celebrity Systems One of the leading company for AV Systems IT Solutions and Security. Celebrity Security - Be Safe With Athena One of our specialities is in the field of celebrity security high profile individuals professional athletes such as footballers and performing artists. For over fifteen years we have successfully protected celebrities safety privacy and lifestyle with an.